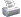Consolidated "Problems Accessing FlyerTalk When Using A VPN" thread
#136
A FlyerTalk Posting Legend
Join Date: Dec 2000
Location: Shanghai
Posts: 41,983
I think I sent a direct message to tech support about Cloudflare acting stupid, but maybe I posted in this forum instead.
Anyway, I use Astrill 90% of the time. Most of my preferred servers are blocked by Cloudflare (only when trying to access FT). I went through a trial and error phase during which I found some that worked intermittently before settling on Santa Clara, which works all the time.
However, I'd like to be able to use the better ones, which is what I relayed to tech support in my message. It shouldn't be especially difficult to whitelist Astrill's (or any other major VPNs') popular servers, right? I'm surprised this particular issue has been persisting for so long; some of my friends have basically stopped using FT as a result.
As an aside, the Cloudflare error page contains no guidance whatsoever.
Anyway, I use Astrill 90% of the time. Most of my preferred servers are blocked by Cloudflare (only when trying to access FT). I went through a trial and error phase during which I found some that worked intermittently before settling on Santa Clara, which works all the time.
However, I'd like to be able to use the better ones, which is what I relayed to tech support in my message. It shouldn't be especially difficult to whitelist Astrill's (or any other major VPNs') popular servers, right? I'm surprised this particular issue has been persisting for so long; some of my friends have basically stopped using FT as a result.
As an aside, the Cloudflare error page contains no guidance whatsoever.
#137
A FlyerTalk Posting Legend
Join Date: Dec 2000
Location: Shanghai
Posts: 41,983
I think I sent a direct message to tech support about Cloudflare acting stupid, but maybe I posted in this forum instead.
Anyway, I use Astrill 90% of the time. Most of my preferred servers are blocked by Cloudflare (only when trying to access FT). I went through a trial and error phase during which I found some that worked intermittently before settling on Santa Clara, which works all the time.
However, I'd like to be able to use the better ones, which is what I relayed to tech support in my message. It shouldn't be especially difficult to whitelist Astrill's (or any other major VPNs') popular servers, right? I'm surprised this particular issue has been persisting for so long; some of my friends have basically stopped using FT as a result.
As an aside, the Cloudflare error page contains no guidance whatsoever.
Anyway, I use Astrill 90% of the time. Most of my preferred servers are blocked by Cloudflare (only when trying to access FT). I went through a trial and error phase during which I found some that worked intermittently before settling on Santa Clara, which works all the time.
However, I'd like to be able to use the better ones, which is what I relayed to tech support in my message. It shouldn't be especially difficult to whitelist Astrill's (or any other major VPNs') popular servers, right? I'm surprised this particular issue has been persisting for so long; some of my friends have basically stopped using FT as a result.
As an aside, the Cloudflare error page contains no guidance whatsoever.

This one happens to be "Los Angeles Supercharged" (one of the better ones for me)
#138
Join Date: Jun 2009
Programs: AMEX Business Centurion
Posts: 418
I use 3 different VPN services (two of them regularly) and all servers seem to be blocked, even the one that was whitelisted manually.
I too know a couple people who are in the same boat and so just don’t use FT anymore. For me it’s cut my visits way down and I just rely on the email notifications to know a little bit about what’s going on here, but generally can’t reply except the once every few weeks for something that I’m compelled enough to make it happen (such as this thread).
FT is the only site I’m having this problem with, and I am certain that many sites on the internet also use Cloudflare, so I’m wondering if maybe there’s a configuration that is set to some extreme degree that is blocking nearly every VPN out there. I wish the right person who understands the issue and has control over the site’s configuration would see this thread and consider lowering the level of that setting to one that would allow SOME VPN servers to access the site. Barring something like that, FT is basically an email newsletter to me now :’(
Lastly for the poster who suggested that everyone just stop using VPN altogether because one website is inaccessible because of it- it reminds me of when that iPhone came out and had a bad antenna design flaw resulting in poor signal when handheld a certain way and Steve Jobs suggested that instead of altering the antenna design that people just hold the phone differently. The internet minions immediately found and posted photos of Jobs holding the iPhone the exact same (supposedly “wrong”) way and the next iPhone came out with a revised antenna set up that fixed the issue. smh
I too know a couple people who are in the same boat and so just don’t use FT anymore. For me it’s cut my visits way down and I just rely on the email notifications to know a little bit about what’s going on here, but generally can’t reply except the once every few weeks for something that I’m compelled enough to make it happen (such as this thread).
FT is the only site I’m having this problem with, and I am certain that many sites on the internet also use Cloudflare, so I’m wondering if maybe there’s a configuration that is set to some extreme degree that is blocking nearly every VPN out there. I wish the right person who understands the issue and has control over the site’s configuration would see this thread and consider lowering the level of that setting to one that would allow SOME VPN servers to access the site. Barring something like that, FT is basically an email newsletter to me now :’(
Lastly for the poster who suggested that everyone just stop using VPN altogether because one website is inaccessible because of it- it reminds me of when that iPhone came out and had a bad antenna design flaw resulting in poor signal when handheld a certain way and Steve Jobs suggested that instead of altering the antenna design that people just hold the phone differently. The internet minions immediately found and posted photos of Jobs holding the iPhone the exact same (supposedly “wrong”) way and the next iPhone came out with a revised antenna set up that fixed the issue. smh
#140
Join Date: Apr 2005
Location: YYZ
Programs: Aeroplan, TD.
Posts: 467
Thanks working again. I just hope that when I turn VPN off anf back on I don't get assigned a new IP address and get the error again.
Last edited by cblaisd; Feb 14, 2022 at 6:27 pm Reason: Fixed quote coding
#141
Join Date: Jan 2016
Location: LON
Programs: BAEC
Posts: 3,910
FT is essentially a 'free' to use site, although I guess that the advertising revenue that IB can get pays the bills necessary to keep it prospering. Regular users will be aware that the site does get targetted by denial of service attacks from time to time, and IB have chosen to use cloudflare to help accelerate the site performance as well as defend against such attacks to help maintain uptime. IB have probably turned on some additional IP filtering to provide some additional front door security to probably minimise the costs of Cloudflare sinking DDOS traffic. CDN providers like Cloudflare typically strike commercial deals on the basis of what's expected as an 'in contract value' and then a PAYG rate for what is unexpected. So by turning on the additional IP filtering my guess is that IB are trying to defend against additional PAYG bandwidth costs from Cloudflare to sink malicious traffic. The reason that the IPs that the public VPNs are on this list is because they are frequently associated with traffic that is suspicious or malicious.
IB are not a charity. This site is commercially run. It's probably getting a lower number of hits and less advertising revenue than it used to due to the downturn in global air traffic, but has been the subject of more DDOS attacks which are expensive to mitigate. We can ask the techs to twiddle the knobs and permit certain IPs but it will be a case of whack-a-mole. Those same tech resources could be otherwise trying to fix other genuine software bugs like the ARG likes, or a dark mode.
I am not anti-VPN, they have a place and purpose. But I would not use them all the time as they obfuscate genuinely useful information from genuine sites that you probably use from time to time and can actually raise your own risk level for logins and financial transactions on the web.
#142
Join Date: Oct 2009
Location: Princeton, NJ
Programs: United 1K, 2MM, Marriott LT Platinum
Posts: 47
I am not anti-VPN, they have a place and purpose. But I would not use them all the time as they obfuscate genuinely useful information from genuine sites that you probably use from time to time and can actually raise your own risk level for logins and financial transactions on the web.
#143
Join Date: Jan 2016
Location: LON
Programs: BAEC
Posts: 3,910
- Who the user is
- What their usual transactions look like
- Where they say they usually located
- IP addresses and locations that they have used in the past
- The reputation of those IP addresses
- Whether the device being used has been seen previously and whether the locale and user agent of the device matches previous transactions
- Etc
Systems will where possible learn the networks that a user typically uses... Work, Home ISP, Mobile ISP, WiFi in their local hospitality venues. If they pop up in a new coffee bar in the same country then this will usually be seen as low risk. But pop up on an IP with poor reputation in another country suddenly, this would hopefully be seen high risk and further checks instigated to protect.
If the user has a regular pattern of using public VPNs then there will be a pattern of jumping about between IP addresses in various places typically with a poor reputation. The login systems can of course profile this as part of this user's typical behaviour, but with a certain amount of blindness, but they won't be able to get a richness of quality data about those connections compared to using network connections directly.
How do I know this - experience of how globally mobile users are profiled by global systems for $dayjob and how public VPNs make a mess of the intelligence that can protect them.
Banks in particular are now using this kind of data to comply with PSD2 (Payment Services Directive) to protect financial transactions. Take a user who makes most of their purchases in Country A, but does most of their online purchases from random IPs in Countries B, C and D. What does the bank do when it sees a new online transaction for Country E, is it high risk?
Public VPNs eliminate a layer of data intelligence and lump your connectivity in with a bunch of other ne'er-do-wells. And the encryption the VPNs typically offer isn't offering anything significant over the native encryption these sites deploy.
Last edited by plunet; Feb 19, 2022 at 4:16 am
#144
A FlyerTalk Posting Legend
Join Date: Dec 2000
Location: Shanghai
Posts: 41,983
I like being able to read sites like NYT and Wapo when I'm logged into FT. I get the fact that there are only about 10 FTers in China at present, but all of us use the same VPN provider, so whitelisting our favorite servers should be easy. My request is for Los Angeles Supercharged. Our friends in Beijing tend to have better luck with others.
#145
Join Date: Apr 2010
Location: Unio Europaea
Programs: BA GGL, AS, Hertz Cirque Présidentielle
Posts: 1,445
I couldn't care less about some automatic geolocation profiling as a means to "protect me", since the very same technology is often times used maliciously for selling my data, forcing advertising on me I don't want or forcing me to be outside some online services. Plus of course other even more malicious forms of evesdropping and ouright espionage. I don't have an issue using an added login verification, but I do take issue with being evesdropped e.g. on a public WLAN or using any Internet connection in a multitude of countries (we aren't only talking the PRC here now). And I didn't yet mention honey pot WLANs.
Suggesting/Advicing me to use a direct connection without an encrypted TCP/UDP tunnel, for the sake of "it's more safe for me" is - with all due respect, utter crap talk and not very recommendable in most scenarios, unless you're happy to expose your traffic. Yes, running HTTPS over a VPN doesn't per say provide added security for a large amount of persons, but you can e.g. revert your DNS queries then, use a strong cipher and also control a bit more fine-grained how the connection is setup. Overall you are indeed better protected then, assuming you've taken steps to have adequate protection for all your online facing user accounts, in which case the geolocation algobased protection is something for the less informed end-users.
As for FlyerTalk, I bypass the overly sensitive WAF as needed, when on a VPN, but it's making the service less practical to use.
#146
Join Date: Jan 2016
Location: LON
Programs: BAEC
Posts: 3,910
As I have said upthread, if you do want an additional layer of security I would suggest setting up a throwaway Linux box or similar to provide a VPN on demand that is dedicated to you, has no reputation issues, turned on only when you need it, configured as you need it, can listen on bespoke ports or protocols, etc. would probably be a better solution. There are plenty of tutorials out there.
#147
Join Date: Oct 2005
Programs: BA GGL & GfL, AA LTP, Marriott (sigh) Ambassador, Hilton Diamond
Posts: 3,227
same and highly annoying as i need the vpn to access other US and UK sites while in the EU and would like to switch over to flyertalk in the middle of work but cannot because i am aligned with the UK or US again so am shut out while on nordVPN.
#148
Join Date: Aug 2004
Programs: AA (EP), Hilton (Diamond), Marriott Bonvoy (Titanium)
Posts: 8,937
VPNs only hide one's IP address, they do nothing to hide one's identity. An IP address may or may not be unique to an individual. As an example, FlyerTalk users tend to travel, which means they likely access the Internet from lots of different places, which has the same IP address hiding as using a VPN. Personally, I use a VPN 100% of the time when away from home as a privacy and security measure. When using Wi-Fi, anyone on the same Wi-Fi network can capture traffic. When using Ethernet, the local network sees the traffic. The primary purpose of VPNs by is to encrypt traffic to hide it from the local network (including other Wi-Fi users). Unfortunately, VPNs are also a great way for attackers to make it harder to block and trace their activity.
#149
Join Date: Aug 2004
Programs: AA (EP), Hilton (Diamond), Marriott Bonvoy (Titanium)
Posts: 8,937
Yes. A number of systems now use a number of criteria to assess the posture of a potential login or a transaction. They will typically use data that they can reasonably collect or know and aggregate the intelligence and posture across all users that use their systems globally. For example (there are other metrics)
[snip]
Public VPNs eliminate a layer of data intelligence and lump your connectivity in with a bunch of other ne'er-do-wells. And the encryption the VPNs typically offer isn't offering anything significant over the native encryption these sites deploy.
[snip]
Public VPNs eliminate a layer of data intelligence and lump your connectivity in with a bunch of other ne'er-do-wells. And the encryption the VPNs typically offer isn't offering anything significant over the native encryption these sites deploy.
#150
Join Date: Jan 2016
Location: LON
Programs: BAEC
Posts: 3,910
Your answer, while detailed and factual, doesn't actually explain how a VPN makes it more likely that a user is an attacker. Blocking access to a site by VPN users is too broad a brush. A site could, just off the top of my head, allow access by users with cookies that indicate recent successful authentication, and send other users to a more-thorough verification check.
By choosing to use the public VPN service you've effectively chosen to walk into some downtrodden bar in a dodgy district somewhere, and although you might have innocently assumed it was an ok place to go for a drink, there's a bunch of people in there just watching their geo-ringfenced Netflix content in the snugs, but at the bar you're actually rubbing shoulders with some of the local criminal lowlife. The police walk in and start asking questions of everyone at the bar, they want to know why you're there and what you're up to associating with the others at the bar, and they're likely to be agresssive with their questioning. They might send you down the station for more questions (2FA challenge), or they eject you out for your own safety for drinking the wrong place and suggest you drink elsewhere in future (Cloudflare 1020 error).
But if you used your native IP address ir a private/corp VPN your reptuation would likely not be besmirched with other internet lowlife who think their VPN is going to protect them. By using your native IP address you're now drinking the bar of your multi-star hotel of a reputable brand where you have status and can earn some points and stuff that FT members care about. The chance that police are going to walk in is already low, and even if they do they would likely be polite and apologise for inconvenicing you.
You're right to question whether the login process of the forum could do more to provide protection, but InternetBrands are using some off the shelf forum software albeit with some customisation. The capabilities of the login authentication is fairly basic as it is for most forums. It doesn't appear to do 2FA, or if it does it will cost more that will have a detrimental impact on the economics of the service. So although I agree it would be good to do more with analysis of the login cookies I guess they are pretty much stuck with what the underlying software provides unless they develop something themselves at considerable cost and ongoing cost to maintain, or they wait for the bulletin board software provider to develop something better or plugins into the big boys (Google, Microsoft, Facebook, Twitter, etc) to reuse an identity you already have. There may be upgrades available that they haven’t implemented, but I don’t have any insight here.
Last edited by plunet; Mar 2, 2022 at 8:42 am Reason: typo